Disable the env endpoint for Spring Boot apps
Did you know that by default, Spring Boot allows you to inspect an application’s configuration, via an unsecured web service?
When running a Spring Boot application, it exposes a number of Endpoints. One of them is the env endpoint, which, according to the docs:
Exposes properties from Spring’s ConfigurableEnvironment.
So if you run a Spring Boot app and go to http://localhost:8080/env, you’ll see this:
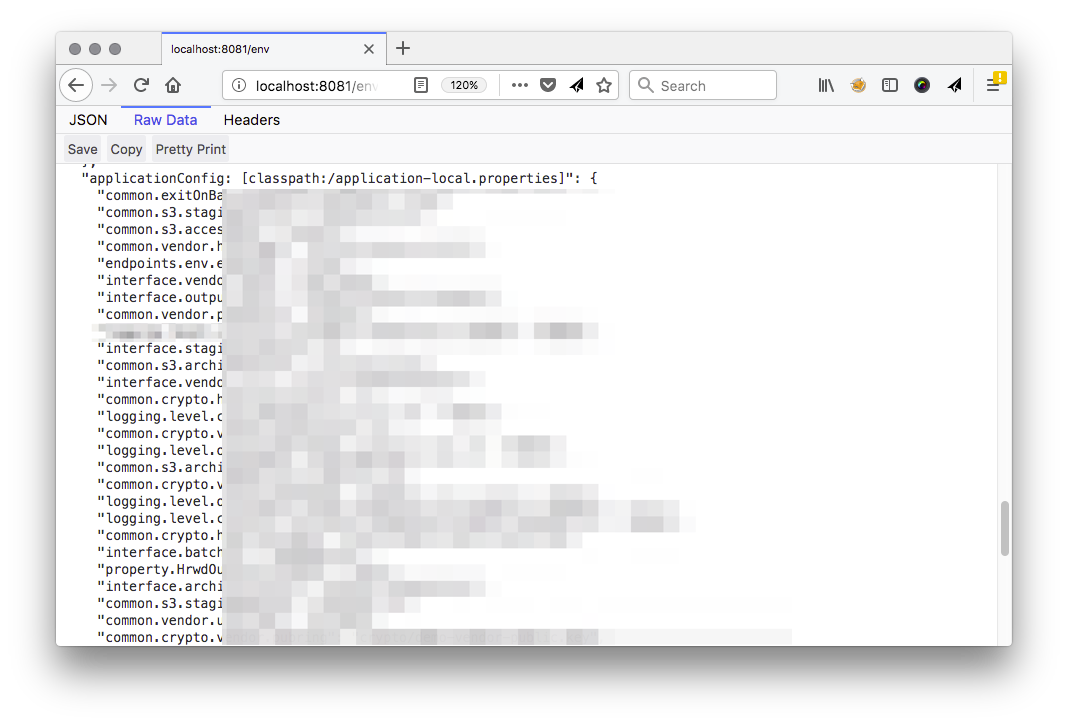
YIKES!
You probably don’t want this enabled in production. It exposes
- environment variables
- Spring config properties (some passwords are masked but not all of them)
- JVM properties
All of this information exposed poses a significant security risk for your apps.
To disable this endpoint, add this property to your application.properties:
endpoints.env.enabled = false
You might want to disable other endpoints too. To read more about them, check the Spring Boot documentation.
Comments
What do you think? You can use Markdown in your comment.
To write code, indent each line with 4 spaces. Or, to paste a lot of code, you can put it in pastebin.com and share the link in your comment.